3 min to read
Certified Red Team Professional (CRTE) Review
CRTE Cerifcate Reveiw

Introduction
Nowadays, Windows Active Directory (AD) is used to administer the networks of almost every organization😁, thus it’s critical for a security expert to be aware of the risks to the Windows architecture.Active Directory is an ever-growing beast with new exploits and abuses discovered regularly😑. Learning how to use this to your advantage as a penetartion tester or even as a red teamer has a lot more practical use cases than any point-and-shoot exploit that could be developed and released.
Course
This course is developed by (Nikhil Mittal) at Altered Security.The focus of the CRTE course is on the use of offensive PowerShell and open-source tools to enumerate and exploit Active Directory. it’s major selling point is in the living-off-the-land approach to Active Directory penetration testing.The course conist of Theortical part (14-hours of video contents+PDFs) and Practical Part (Over 300 of torture😥)
The course outline is the following:
Offensive Side:
- Offensive Powershell
- Domain Enumeration
- Local Privilege Escalation
- PowerShell Remoting (and WinRS)
- Domain Privilege Escalation
- Lateral Movement
- Offensive .NET
- Domain Persistence
- Cross Trust Attacks
- Cross Forest Attacks
Defensive Side
- Protect and Limit Domain Admins
- Isolate administrative workstations
- Secure local administrators
- Time bound and just enough administration
- Isolate administrators in a separate forest and breach containment using
- Tiers and ESAE
One thing you might notice is that the section on defense and detection is quite larger than the (CRTP). This is an interesting feature, but it’s not the course’s primary selling point as the course focus more in the red part but it’s good for blue teams to gain some knowlege on the red mindset and how to defend against it.
Labs
I really enjoyed working my way through the lab environment and getting to leverage abuses that I haven’t really had a chance to use up until now.As the CRTP the lab is accessable either through VPN or through RDP access over Guacamole.The lab simulates real world attack-defense scenarios and require you to start with a non-admin user account in the domain and work your way up to enterprise admin of multiple forests. The focus is on exploiting the variety of overlooked domain features and not just software vulnerabilities.The architecture of the lab can be viewed below.
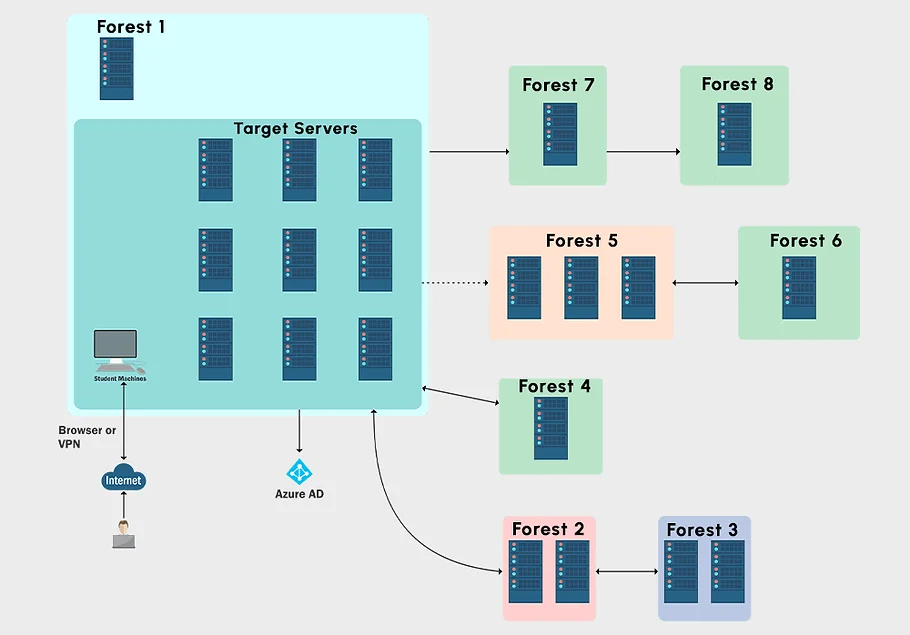
And to be true,I’ve ran into one problem where where one of the DCs in the lab quit responding for some reson which made various tools and exploits that relied on them being up didn’t work but you can contact the support and they will easily handle it.🤗
Exam
Just like CRTP, you will access the exam through the student portal.The exam enviroment will take between (10-15) minute to ready thenyou’re on your way! You have (48 hours) to complete the exam objectives with another (48 hours) to submit your exam report.The exam is an assumed breach , you will have a low-privilege access on your foothold machine ,so obvilsoly you will need to priv esc your privilges🤭 and from here where the tourture begins but an advice when you ever feel that you hit a massive roadblock enumerate as hard as you can,I can tell you that almost every roadblock that will face you during the exam the solution is in the enumeration.😁
Exam Tips
- Pick the right time to start the exam.
- If you want to use BloodHound, set it up locally before you start the exam. Ensure the version of the ingestor will work with your version of BloodHound!
- Enumerate…enumerate…enumerate.
- Don’t panick.You have 48 hours to knock this thing out.

Comments